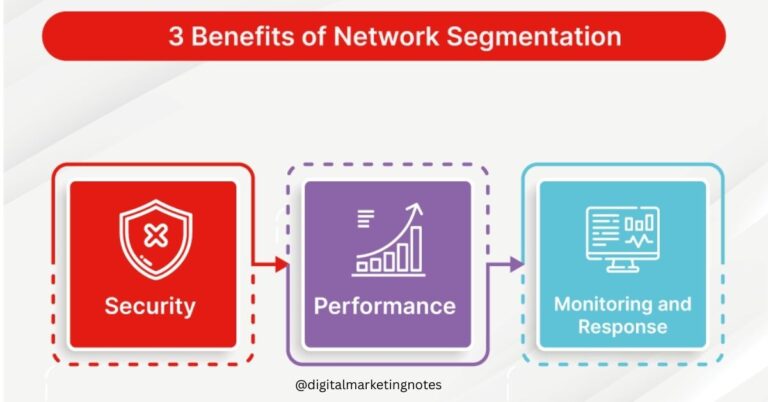
Network Segmentation and How it Can Prevent Ransomware
Ransomware is on the rise. In 2020, ransomware Network Segmentation attacks surged by 150% , with the average attack extorting as much as $170,000 (although cybercriminal groups such as Maze, Egregor, and…