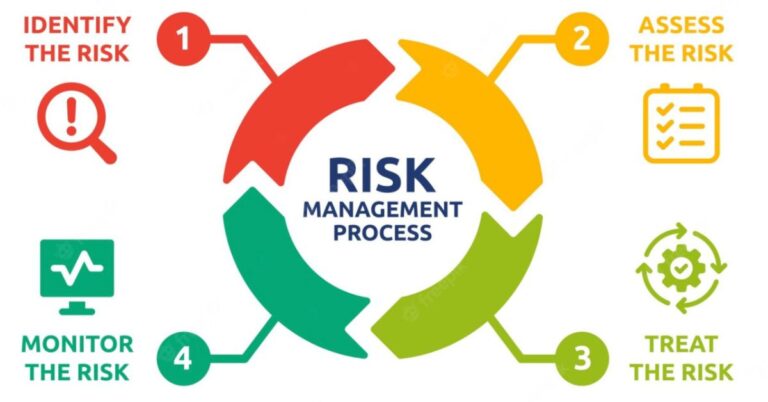
How to Perform a Cybersecurity Risk Assessment
What is a Cybersecurity Risk Assessment? A Cyber Risk Assessment is a systematic process that identifies, analyzes, and evaluates potential cyber risks across an organization’s networks, devices, applications, and users….